مثال: خوادم بريد إلكترونية
الإحصائيات العامة · سلسلة زمنية
رسم بياني مكدس يوضح عدد عناوين IPv4 وIPv6 التي تم اكتشافها وهي تستجيب كل يوم خلال الأسبوع الماضي، على مستوى العالم، ومميزة بالعلامة CVE-2023-36439
الإحصائيات العامة · تصوُر · جدول
جدول يوضح عدد عناوين IPv4 وIPv6 التي تم اكتشافها وهي تستجيب كل يوم خلال اليوم الماضي، على مستوى العالم، ومميزة بالعلامة CVE-2023-36439.
الإحصائيات العامة · خريطة الشجرة
خريطة شجرة توضح عدد عناوين IPv4 وIPv6 التي تم اكتشافها في تاريخ محدد، والمميزة بالعلامة CVE-2023-36439، مع تمثيل العدد لكل بلد بشكل تناسبي.
من خلال النقر على جزء من الدولة يمكن الاطلاع على تفاصيل للمصادر والإحصاءات العامة التي تم الحصول عليها من CIA world factbook.
مثال: أجهزة CWMP المكشوفة
الإحصائيات العامة · سلسلة زمنية
مخطط زمني يوضح ما يعادل عامين من البيانات التاريخية (الحد الأقصى للنطاق في لوحة المعلومات العامة) - في هذه الحالة بالنسبة للمملكة العربية السعودية يوضح عدد عناوين IP لجهاز CWMP المكشوف التي يتم اكتشافها كل يوم.
ملاحظة: هذا الرسم البياني يوضح تحسنًا كبيرًا من حيث التعرض لـ CWMP في نهاية يناير 2023
مثال: حالات MISP
إحصائيات جهاز إنترنت الأشياء · تصوُر · رسم بياني شريطي
يمكن أخذ بصمات لعدد من الأجهزة والحلول البرمجية أثناء المسح. يوضح هذا الرسم البياني (على مقياس لوغاريتمي) عدد عناوين IP التي تم اكتشافها كل يوم في المتوسط، على مدار الشهر الماضي، مع تشغيل حالات MISP.
مثال: الثغرات الأمنية المستغلة
Attack statistics: Vulnerabilities · مراقبة
أهم 100 محاولة لاكتشاف ثغرات أمنية قابلة للاستغلال (من بين أجهزة مراقبة Shadowserver الموجودة في مصائدنا)، تم تصنيفها مبدئيًا حسب عدد عناوين IP الهجومية الفريدة خلال اليوم الماضي.
النقر فوق خيار الخريطة يتيح للمستخدم التبديل بين أنواع المضيف "المصدر" و"الوجهة" (أي مهاجمة تحديد الموقع الجغرافي لـ IP مقابل تحديد الموقع الجغرافي لـ IP الخاص بالمصيدة).
ملاحظة: تحديد الموقع الجغرافي المهاجم قد يمثل أو لا يمثل بدقة موقع المهاجم نفسه.
مثال: Interpreting events
استخدام لوحة البيانات للمساعدة في تفسير الأحداث: زيادة غريبة في أجهزة CWMP المكشوفة (يُعتقد أن أجهزة الراوتر المنزلية من Huawei) في مصر، يتم تتبعها بهجمات Mirai ناشئة من نفس البلد.
ملاحظة: عملت مؤسسة Shadowserver مع فريق nCSIRT المصري بغرض الإخطار والمعالجة.
إحصائيات جهاز إنترنت الأشياء · سلسلة زمنية
ملاحظة زيادة في عدد أجهزة إنترنت الأشياء المكشوفة التي تم الإعلان عنها على البنية التحتية المصرية في 5/1/2023.
إحصائيات جهاز إنترنت الأشياء · خريطة الشجرة حسب الشركة المصّنعة
يُظهر التنقل للأمام والخلف عبر التواريخ أن الأجهزة من المحتمل أن تكون أجهزة Huawei المرئية حديثًا اعتبارًا من 5/1/2023.
الإحصائيات العامة · سلسلة زمنية
الارتفاع المرتبط بذلك في اكتشافات بروتوكول CWMP المكشوفة من المسح المطابق للزيادة التي ظهرت في 5/1/2023.
أجهزة استشعار مصيدة Shadowserver حددت الأجهزة المصرية المخترقة التي يُشتبه أنها تشن هجمات Mirai وهجمات القوة الغاشمة.
وما يقابلها من هجمات Telnet Brute Force الصادرة من الأجهزة المصرية المختَرقة.
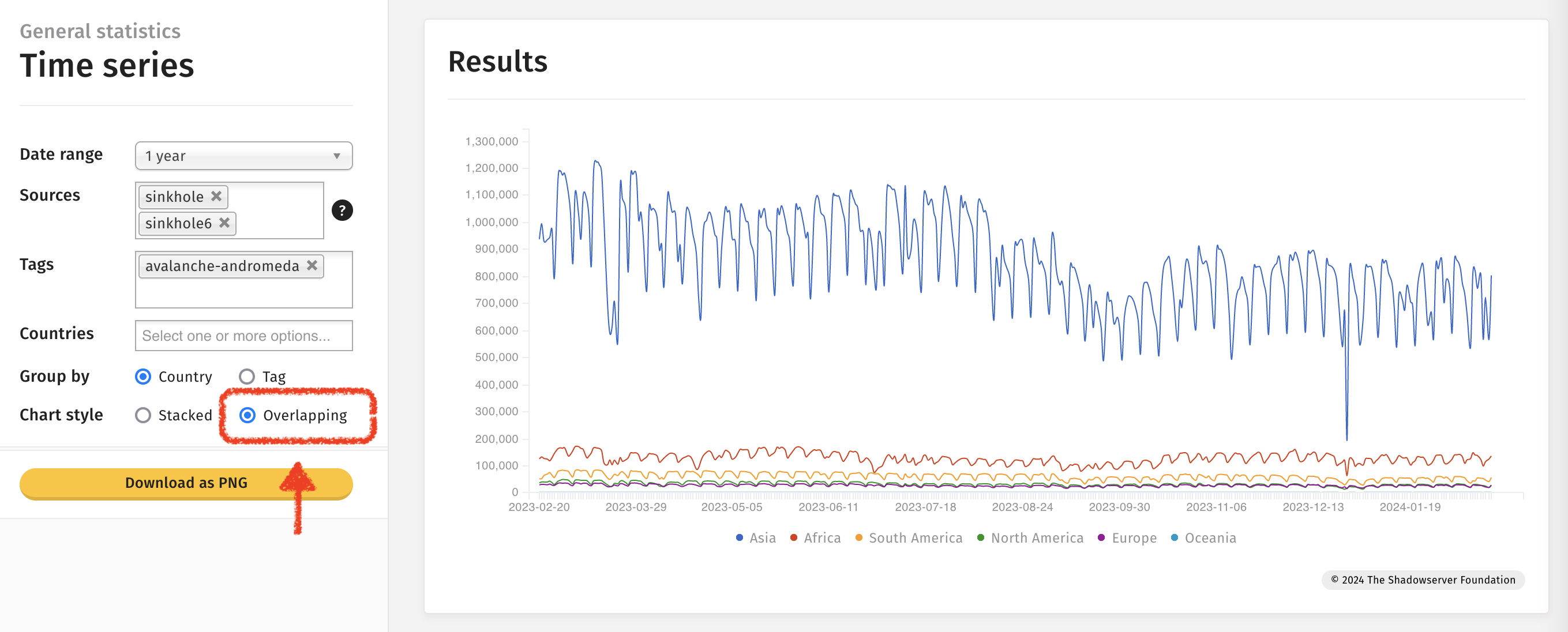
إن استخدام مصادر متعددة واختيار خيارات العلامة والتداخل (Tag and Overlapping) يتيح تقديم الملاحظات على نفس الرسم البياني.
مثال: تقارير خاصة
تصدر Shadowserver أحيانًا تقارير خاصة لمرة واحدة. إننا نعلن عن البيانات على X/Twitter وعلى موقعنا على الويب - ولكنك بعد الحدث قد ترغب في معرفة التواريخ الهامة. إن إحدى طرق معرفة التواريخ هي استخدام مخطط Time Series للبحث عن تواريخ التقرير الخاص - وبعد ذلك يمكنك نقل هذه التواريخ إلى تمثيلات أخرى مناسبة بشكل أفضل لإحصاءات اليوم الواحد (مثل الخرائط أو خرائط الأشجار). تحتوي التقارير الخاصة على مجموعة مصادر على special على لوحة البيانات.
البحث عن تقارير خاصة على مخطط سلسلة زمنية:
خريطة شجرة لمثال لتقرير خاص موجود بتاريخ 29/1/2024:
للحصول على قائمة بالتقارير الخاصة، يرجى مراجعة قائمة التقارير الموجودة على main website. التقارير الخاصة سوف يتضمن اسمها كلمة "Special".
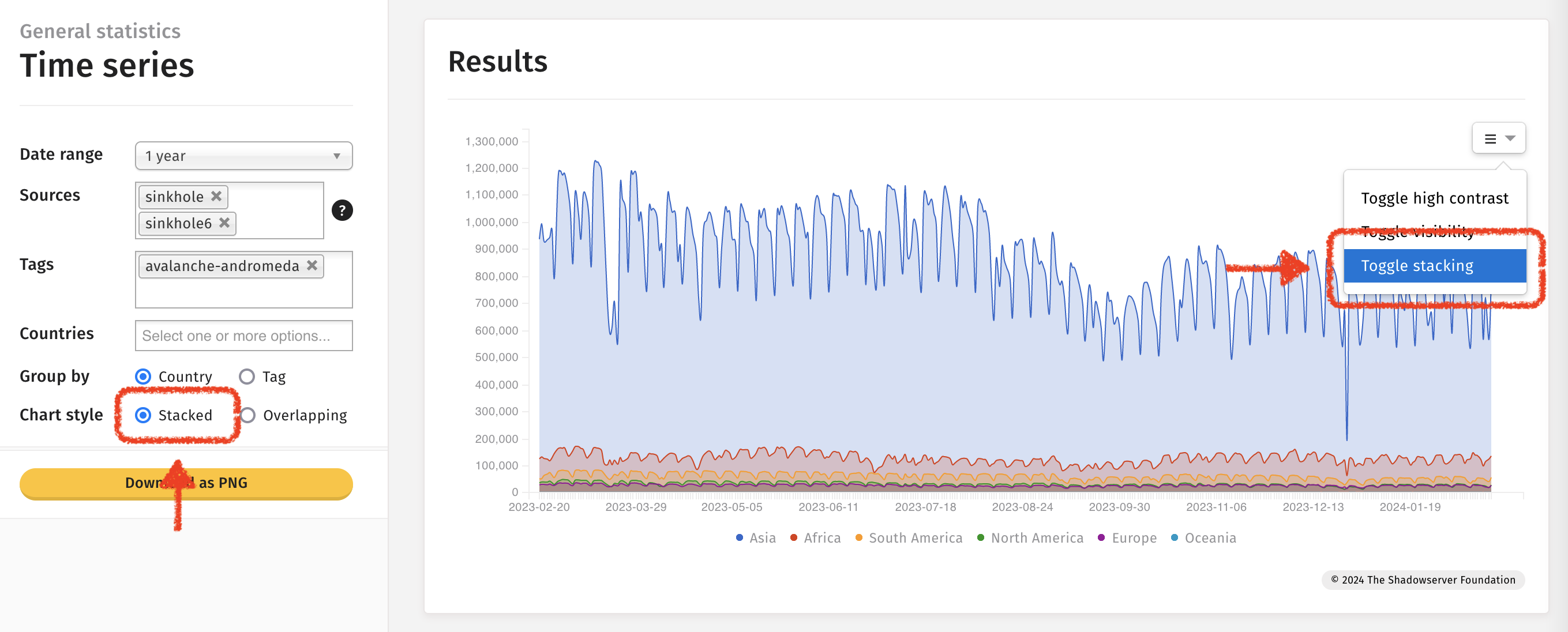
مثال: Time-series charts
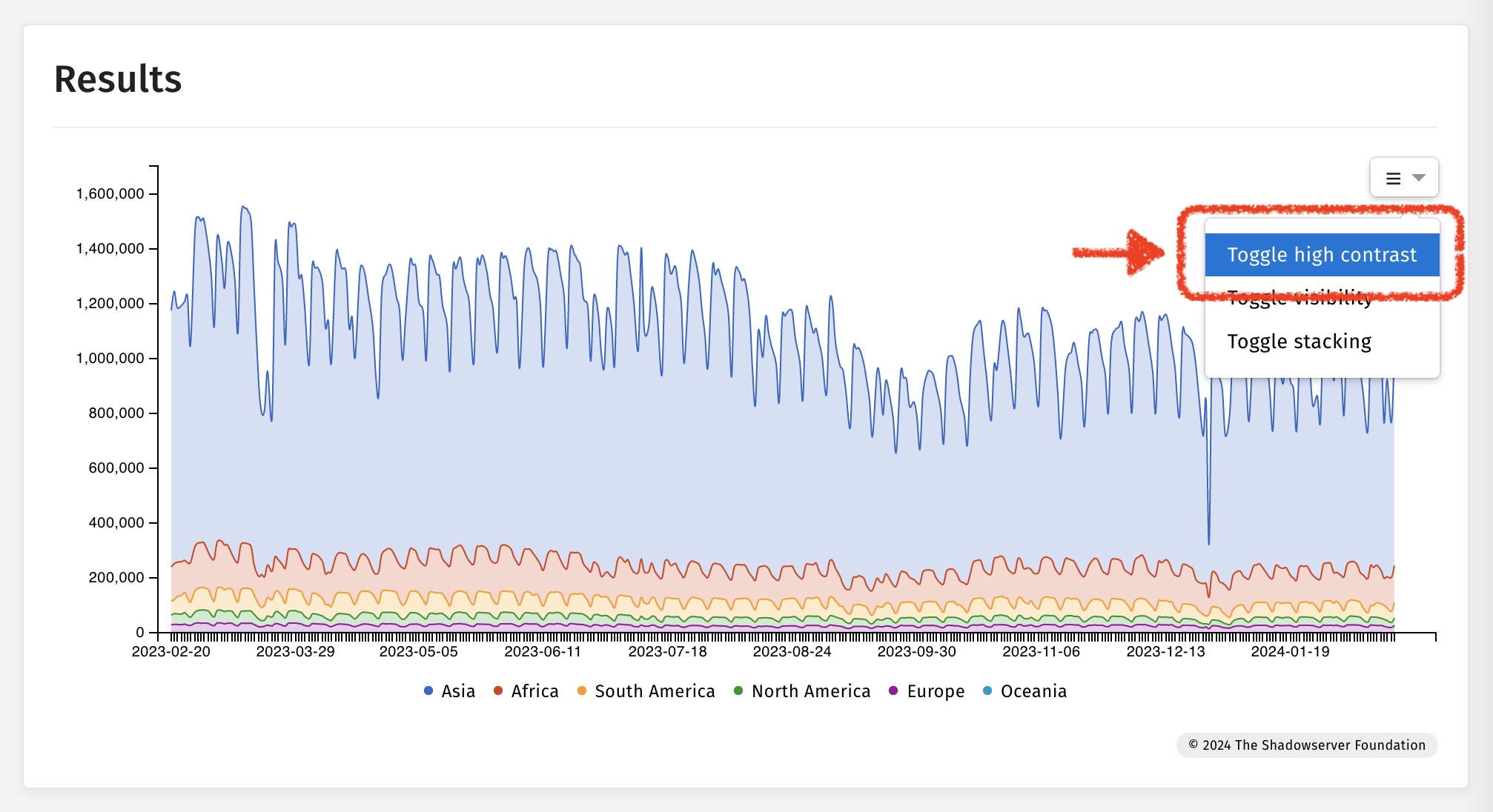
تبديل التباين العالي
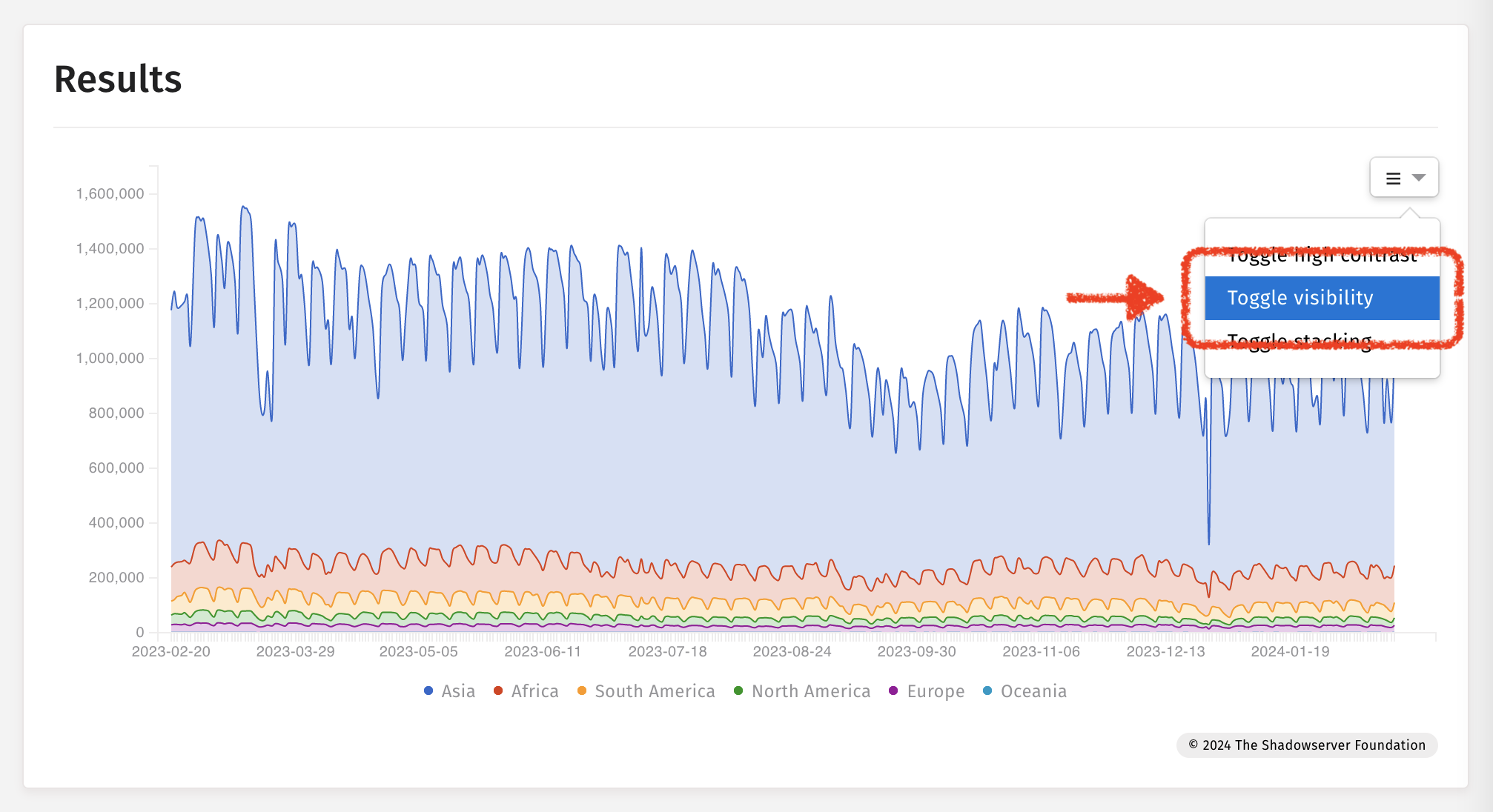
تبديل الرؤية
تبديل التكديس